THIS CERTIFICATION IS AUTHENTIC AND ACCEPTED BY EMPLOYERS. HOW ? Read more
What You get
with this Course
Metasploit Framework I Penetration Testing Course I Certification

WHY IS THIS VIDEO TRAINING ONLINE CERTIFICATION HIGH IN DEMAND?
What is Metasploit framework?
The Metasploit Project is a computer security initiative that aids in the creation of IDS signatures, penetration testing, and information about security flaws.
Cybercriminals and ethical hackers can both use the sophisticated Metasploit framework to scan servers and networks for systemic weaknesses. It may be used with most operating systems and is highly customizable because it is an open-source framework.
The pen testing team can use ready-made or custom code with Metasploit to introduce it into a network and probe for vulnerabilities. Once flaws are discovered and recorded, a different variation of threat hunting can be used to prioritize fixes and address systemic weaknesses.
It is an open-source initiative that provides resources for the general public to create scripts and investigate security flaws. It enables network managers to identify security concerns on their network and to describe which vulnerability needs to be defined first.
It is a particular project type that makes software for pen (penetration) testing easier. Additionally, it provides tools to automatically compare a program's vulnerability and its patched (repaired) version. Additionally, advanced evasion and anti-forensic tools are provided. A few of these tools were developed for the Metasploit framework.
The Metasploit Framework is one of the Metasploit Project's greatest works of art. A software environment for creating, testing, and deploying exploits is called Metasploit Framework. It might be used as a pen-testing system, to develop tools for security testing, and to exploit modules. It was initially created by HD Moore as a portable network tool.
This framework is an extremely effective tool. Both ethical hackers and cybercriminals can use it to scan servers and networks for recurring vulnerabilities. Being an open-source framework, it is simple to use and adapt to different operating systems.
What is penetration testing?
An authorized simulated cyber attack on a computer system is known as a penetration test, often referred to as a pen test or ethical hacking, and is carried out to examine the system's security. This is distinct from a vulnerability assessment. The test is run to find both strengths and weaknesses, allowing a thorough risk assessment to be completed. Weaknesses (also known as vulnerabilities) include the possibility for unauthorized parties to access the system's features and data.
Penetration testing, often known as a pen test or ethical hacking, is the authorized simulation of a cyber attack on a computer system that is used to assess the system's security. An assessment of vulnerabilities is not the same as this. The test is conducted in order to identify both strengths and weaknesses, enabling a thorough risk analysis. Vulnerabilities, which are another name for weaknesses, include the potential for unauthorized parties to access the system's functions and data.
What is the importance of penetration testing?
To Identify and Address Vulnerabilities
It is typical for flaws and vulnerabilities to surface during the design and implementation of a network or system that serves the entire enterprise. Hackers who stay on the cutting edge of technology and rely on their experience in exploiting known vulnerabilities found in these systems can take advantage of these bugs.
To lower Network downtime and save on remediation costs
It can take a long time and money to recover from a security breach, and your organization may not even be able to operate as a result. According to an IBM report, the average cost of a data breach in 2020 would be $3.86 million, and it will take 207 days on average to uncover one.
A penetration test, on the other hand, is proactive by nature and finds high-risk exploitable holes in your system. It is advised that businesses carry out frequent penetration tests at least once or twice a year to maintain business continuity.
Maintains continued trust
A data breach can harm a company's reputation and result in future losses because customers may begin to lose faith in it. To secure security and preserve the trust of customers in your brand, it is essential to run frequent pen tests. Systematic security audits reassure stakeholders, partners, suppliers, and clients.
Create Effective Security Measures
A penetration test provides your business with useful data regarding found security flaws and their present and potential effects on the system's functioning and performance. An expert penetration tester will give you a list of suggestions outlining the severity of the problem, the deadline by which it should be rectified, and how to build a solid information security system that will allow you to objectively prioritize your future cybersecurity efforts.
Choose a reputable and experienced company to do your penetration tests because, despite the use of automated technologies, the focus is still on manual skills, making the professional expertise and experience of the testers the most valuable asset.
Facilitate new business acquisitions and develop an improvement road map
Penetration testing makes the process of acquiring new businesses more effective. A new business acquisition necessitates the adoption of a new IT network, which introduces a number of potential vulnerabilities. Any security flaws in the other company's system have now been transferred to yours.
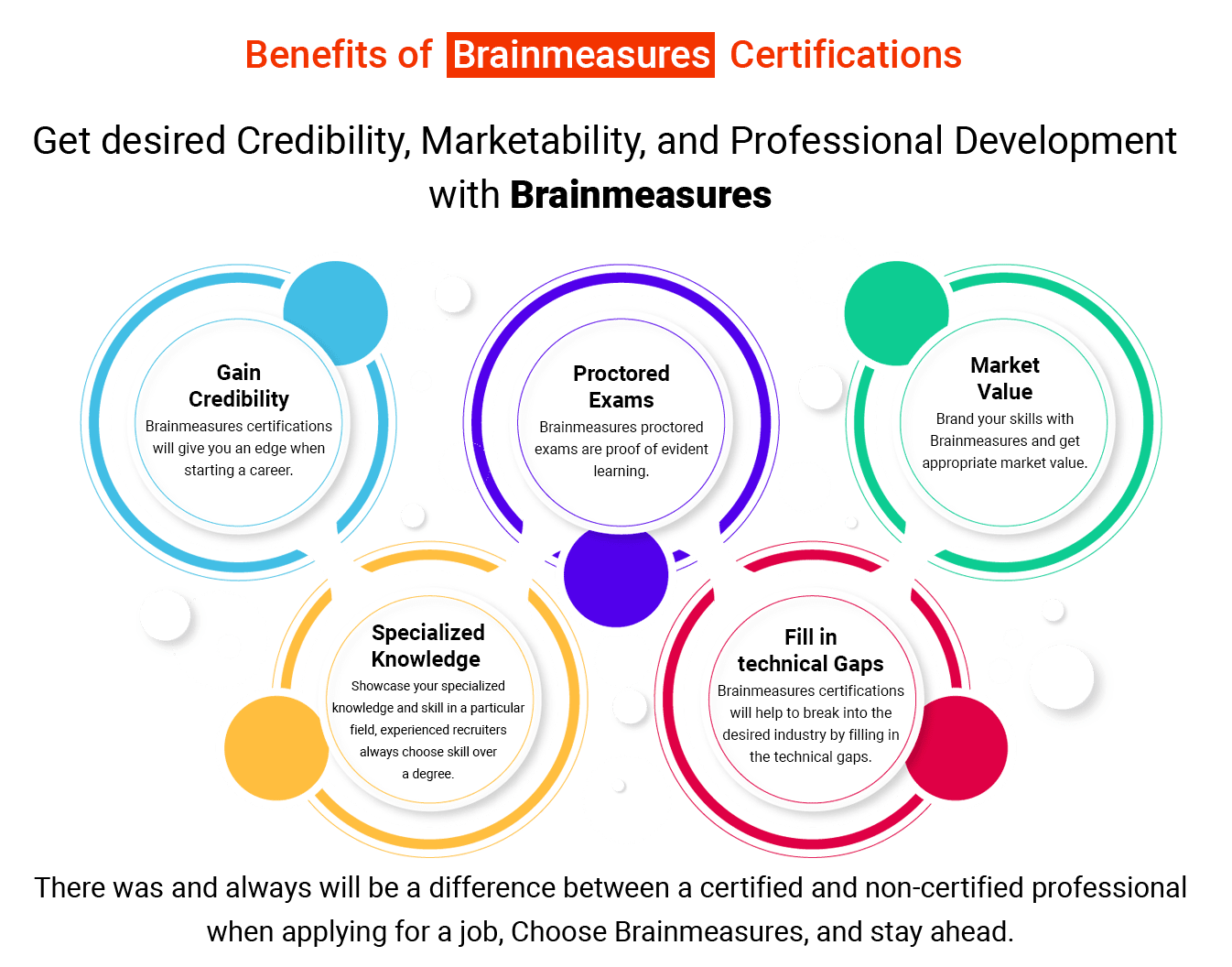
Why Brainmeasures?
At Brainmeasures, you will be provided with high-end courses after which you can get a hard copy certificate. You only have to clear a test and you will get a certificate which assures a bright future by securing your job. You will be hired by great companies in no time.
1300 eBook Courses (Technical and Non-Technical)
20000+ Video Courses (Technical and Non-Technical)
Course Syllabus
| Getting Started | 11 lectures | 17 mins |
| HTML and foundation | 11 lectures | 17 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| CSS and foundation | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| Making Responsive Website | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| Learn Sass less Scss | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| Learn about Cpanel and file uploads | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
Do you want this course
to learn
LIVE
?
Enroll in this course now and avail all the benefits.

Learn from industry
Experts
LIVE
?
Learn One-to-One Live Course - Coming Soon.



Brainmeasures Certifications are acknowledged globally because the tests are conducted under the strict vigilance of trained proctors and are recorded which makes Brainmeausres testing system the most authentic testing platform.
Enroll NowOur Hiring Partners
Brainmeasures certified Professionals work with global leaders.

Corporate Training
If you want to give the Trending technology experience to your esteemed employees, we are here to help you!
CONTACT CORPORATE CO-ORDINATOR
What makes Metasploit Framework I Penetration Testing Course I Certificationunique?
VIDEO ONLINE COURSE
The video online course is well-structured and comprehensive.
EASY TO UNDERSTAND
The topics are organized in proper sequence to enable the candidate understand them easily.
SELF-EXPLANATORY
Easy to understand and implement in real life.
MORE ATTRACTIVE
Sufficient pictures, tables, graphs have been provided to make this online Course more attractive to the readers.
PROCTOR SURVELIANCE
Final certification exam conducted under surveillance of trained human proctor.
HARD COPY SHIPPED
We will ship your hard copy anywhere you ask for.
-

- We will ship your hard copy anywhere you ask for.
- SAMPLE HARDCOPY CETIFICATE
-

- Immediately after taking the test you can check your scores with detailed.
- Immediately download soft copy certificate.
- VIEW ANALYSIS REPORT
-

- ENROLL FOR Metasploit Framework I Penetration Testing Course I Certification - VIDEO COURSE AND CERTIFICATION PROGRAM
- REGISTER NOW
-

- Online Video course by Highly qualified Trainers.
-

- If you have any query our trainers are accessible easily.
- Send your questions and get answers within 7 working days.
-

- Final exam is proctored – you will be monitored throughout, this is done using our high-end Proctor software, so that you need not go to any special location but take it from your own PC.
- This testing format matches world-class testing standards.
- Certificate will mention wording proctored to prove the authenticity of your knowledge.
-

- You can take any number of retakes if you are not satisfied with your score or failed to pass.
- Test re-takes are paid, each retake is worth $ 50.
-

- Earn high.
- Brainmeasures certificates are honoured by employees worldwide.
- Get desired position in your organization.
TAKE A FREE TEST
Metasploit Framework I Penetration Testing Course I Certification
Take free practice test now
Reviews ( click here to Read all )
Why choose Us
In today’s corporate world, a single wrong decision can cost you millions; so you cannot afford to ignore any indemnities you may incur from a single wrong hiring decision. Hiring mistakes include the cost of termination, replacement, time and productivity loss while new employees settle into their new job.
Our Mission
Our Mission is simply to help you attain Course Name knowledge which is at par with best, we want to help you understand Course Name tools so that you can use them when you have to carry a Course Name project and make Course Name simple and learnable.