THIS CERTIFICATION IS AUTHENTIC AND ACCEPTED BY EMPLOYERS. HOW ? Read more
What You get
with this Course
CyberSecurity I Testing I Security Assessment Certification Course

WHY IS THIS VIDEO TRAINING ONLINE CERTIFICATION HIGH IN DEMAND?
What will you learn from this course?
Penetration testing
Software testing
Security management tasks
Vulnerability assessment
What is Cyber Security?
Computer security (also known as cybersecurity) or information technology security refers to safeguarding computer systems and networks against information disclosure, theft, and damage to their hardware, software, or electronic data, as well as from disruption or misdirection of the services they offer (IT security).
For systems connected to the internet, including their hardware, software, and data, cybersecurity is the defense against cyber threats. This method is used by both individuals and companies to stop unauthorized access to data centers and other digital systems.
A strong cybersecurity strategy can provide a good defense against malicious attacks that aim to access, change, remove, destroy, or extort sensitive data and systems that belong to a company or user.
What is Security Assessment or testing?
The process of testing and/or assessing management, operational, and technical security controls in an information system to see how well they are being implemented, functioning as intended, and providing the desired results with regard to the system's security needs.
Software testing with a security focus identifies risks, dangers, and weaknesses in software applications and guards against nefarious intrusions. The goal of security tests is to find any flaws or vulnerabilities in the software system that could allow workers or outsiders to steal information, money, or reputation from the organization.
Key security controls in applications are found, evaluated, and put into place by a security risk assessment. Additionally, it emphasizes avoiding application security flaws and vulnerabilities. An organization can view the application portfolio holistically—from the viewpoint of an attacker—by conducting a risk assessment. It aids managers in deliberating wisely about the use of resources, tools, and security control implementation. Therefore, conducting an assessment is a crucial step in the risk management process of an organization.
Why security testing is important for business?
The main objective of security testing is to determine the system's threats and assess any potential vulnerabilities so that threats can be encountered and the system can continue to operate without being compromised. Additionally, it aids in identifying any security risks that might be present in the system and enables programmers to solve issues.
Cost cutting
The adage "prevention is better than cure" is one that we have all heard. In light of this, utilizing security testing can significantly reduce the cost of recovery and fixing after a compromise. A small portion of the costs related to recovery following a breach may also be included in the cost, along with the procurement of tools and technology like vulnerability scanners.
Important for startups
These services frequently gather and extensively utilize data that has been gathered from end users or clients. Operational data and data that are kept in repositories are separated out into separate categories in this data. If any of these data are hacked, it poses a serious risk of data misuse for the organization and makes the information public.
Users frequently rely on online banking and payment platforms to complete transactions and disclose a lot of sensitive and important data on these applications and platforms. Any security lapses, no matter how serious, might erode customer trust, the organization's integrity, and its brand, which would ultimately have an impact on revenue.
Customer Faith
To ensure customer trust, security testing is crucial for another reason. Security testing is incredibly important for maintaining your consumer base and safeguarding your company's reputation. Security testing not only guarantees that your business has a strong security system that helps gain and keep a client base, and hence customer trust, but it is frequently a necessity to get accredited and certified.
Management of Risk
Overlooked and unmanaged vulnerabilities and flaws frequently have the potential to develop into real dangers. As a result, security testing can aid your business in defending against such flaws and fending off threats, but it must be carried out before hackers become familiar with your application and start taking advantage of its vulnerabilities. Furthermore, security testing becomes even more important if you use third-party applications, outsourced services, or cloud-based services.
What are the features of cybersecurity testing or assessment?
The following are the features of security testing:
Authentication
Authorization
Confidentiality
Availability
Integrity
Non-repudiation
Resilience
How does cybersecurity testing work?
The depth of security assessment models is influenced by variables including size, growth rate, resources, and asset portfolio. If an organization is limited by time or money, it can nonetheless conduct broad assessments. The specific mappings between assets, associated threats, identified risks, effects, and mitigation controls, however, may not always be provided by generalist assessments.
A more thorough examination is required if the findings of the generalized assessment don't show a strong enough association between these areas.
Who can this course?
This course is for the persons who are
Internet security expert
reputable hackers
Those who manage networks
Computer programmers
engineers for data
Course Syllabus
| Getting Started | 11 lectures | 17 mins |
| HTML and foundation | 11 lectures | 17 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| CSS and foundation | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| Making Responsive Website | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| Learn Sass less Scss | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
| Learn about Cpanel and file uploads | 17 lectures | 87 mins |
| Some title goes here | Preview | 01:42 |
| Welcome guide document | 10 Pages | |
| Some title goes here | 07:42 | |
| 2 Some title goes here | 07:42 | |
| Hello Some title goes here | 07:42 | |
| This is Some title goes here | 07:42 |
Do you want this course
to learn
LIVE
?
Enroll in this course now and avail all the benefits.

Learn from industry
Experts
LIVE
?
Learn One-to-One Live Course - Coming Soon.



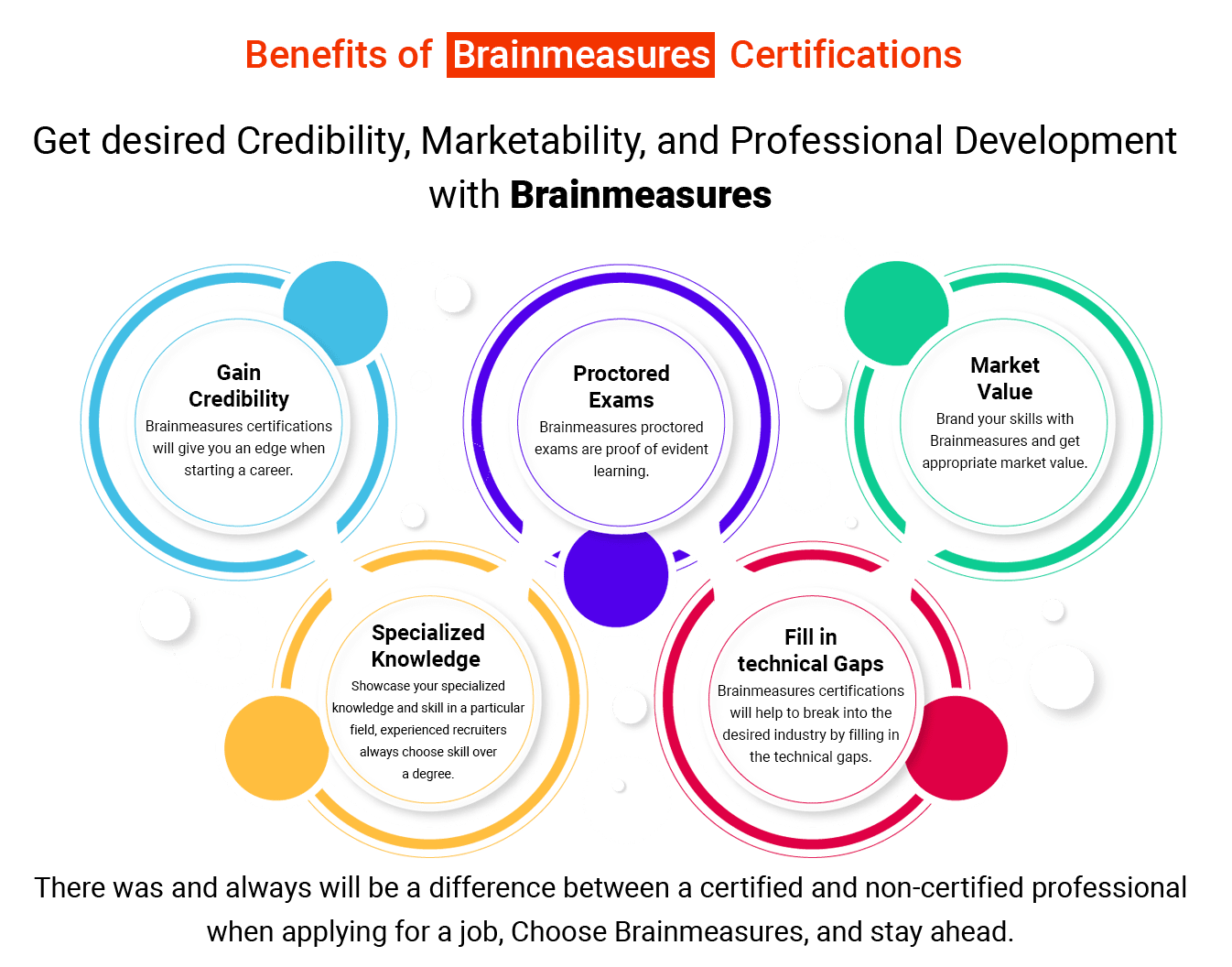
Brainmeasures Certifications are acknowledged globally because the tests are conducted under the strict vigilance of trained proctors and are recorded which makes Brainmeausres testing system the most authentic testing platform.
Enroll NowOur Hiring Partners
Brainmeasures certified Professionals work with global leaders.

Corporate Training
If you want to give the Trending technology experience to your esteemed employees, we are here to help you!
CONTACT CORPORATE CO-ORDINATOR
What makes CyberSecurity I Testing I Security Assessment Certification Courseunique?
VIDEO ONLINE COURSE
The video online course is well-structured and comprehensive.
EASY TO UNDERSTAND
The topics are organized in proper sequence to enable the candidate understand them easily.
SELF-EXPLANATORY
Easy to understand and implement in real life.
MORE ATTRACTIVE
Sufficient pictures, tables, graphs have been provided to make this online Course more attractive to the readers.
PROCTOR SURVELIANCE
Final certification exam conducted under surveillance of trained human proctor.
HARD COPY SHIPPED
We will ship your hard copy anywhere you ask for.
-

- We will ship your hard copy anywhere you ask for.
- SAMPLE HARDCOPY CETIFICATE
-

- Immediately after taking the test you can check your scores with detailed.
- Immediately download soft copy certificate.
- VIEW ANALYSIS REPORT
-

- ENROLL FOR CyberSecurity I Testing I Security Assessment Certification Course - VIDEO COURSE AND CERTIFICATION PROGRAM
- REGISTER NOW
-

- Online Video course by Highly qualified Trainers.
-

- If you have any query our trainers are accessible easily.
- Send your questions and get answers within 7 working days.
-

- Final exam is proctored – you will be monitored throughout, this is done using our high-end Proctor software, so that you need not go to any special location but take it from your own PC.
- This testing format matches world-class testing standards.
- Certificate will mention wording proctored to prove the authenticity of your knowledge.
-

- You can take any number of retakes if you are not satisfied with your score or failed to pass.
- Test re-takes are paid, each retake is worth $ 50.
-

- Earn high.
- Brainmeasures certificates are honoured by employees worldwide.
- Get desired position in your organization.
TAKE A FREE TEST
CyberSecurity I Testing I Security Assessment Certification Course
Take free practice test now
Reviews ( click here to Read all )
Why choose Us
In today’s corporate world, a single wrong decision can cost you millions; so you cannot afford to ignore any indemnities you may incur from a single wrong hiring decision. Hiring mistakes include the cost of termination, replacement, time and productivity loss while new employees settle into their new job.
Our Mission
Our Mission is simply to help you attain Course Name knowledge which is at par with best, we want to help you understand Course Name tools so that you can use them when you have to carry a Course Name project and make Course Name simple and learnable.